2025-12-06 06:00:08
This article is copublished with USA Today.
\ Welcome to The Markup, where we use investigative reporting, data analysis, and software engineering to challenge technology to serve the public good. Sign up for Klaxon, a newsletter that delivers our stories and tools directly to your inbox.
As The Markup was investigating whether Instagram practiced shadowbanning—covertly hiding what people post without telling them—we heard from so many Instagram users that they felt helpless after the platform removed their content or kept them from commenting and posting.
Read the entire series:
We also heard that the appeals process left people frustrated. There’s not much documentation on when exactly users can appeal Instagram’s decisions; as The Markup found, identical content posted by different users can be treated completely differently.
\ If you think you’ve been shadowbanned on Instagram—or if the app has notified you that it has removed your content or limited your account in some way—here’s what you can do.
\ One note: Instagram often changes app settings without notice, so these steps work as of the time this story was published—but if they don’t, you may want to hunt around in a “Help” section.
Under “Account Status,” users can see the content Instagram removed, what features they’re currently banned from using, or if they’re at risk of having their account deleted by Instagram and why.
\ Business and creative accounts can check if they can be recommended to people who aren’t following them and which, if any, of their posts went against Instagram’s recommendation guidelines. These accounts can also see how violations may be affecting their ability to use Instagram’s monetization tools.
\ Instagram claims that if a user’s post is removed, the user is able to request a review “for the vast majority of violation types” except when there are “extreme safety concerns, such as child exploitation imagery.” If Instagram allows a user to request a review, Account Status is where they can submit it.
\ But what shows up under Account Status isn’t the complete picture. The Markup found that users can’t always see what actions Instagram has taken when it believes someone’s account or content doesn’t follow guidelines, despite its claims otherwise. Certain restrictions, such as banning a user from being able to comment, did not show up under “Features you can’t use.”
\ We repeatedly found that content removed for going against guidelines on “spam” or “dangerous organizations and individuals” didn’t show up in the “Removed content” section under Account Status, though it shows up on another part of the platform (check out our next section).
\ Still, it’s worth checking Account Status to see if there’s any information on whether your account has been banned or restricted.
\ On a desktop or mobile browser, you can go to Account Status directly.
Go to your Profile page by tapping on the 👤 person icon in the lower-right corner of the screen.
Click on the ☰ menu icon in the upper-right corner of the screen.
Scroll down and select “Account Status.”
If you can’t find your removed content under Account Status, sometimes it will show up under “Violations.”
\ On a desktop or mobile browser, go to the Help page, select “Support Requests,” then “Violations.”
Go to your Profile page by tapping on the 👤 person icon in the lower-right corner of the screen.
Click on the ☰ menu icon in the upper-right corner of the screen.
Select “Settings and privacy.”
Scroll down and select “Help.”
Select “Support Requests.”
Select “Violations.”
If Instagram took down your post and you don’t agree that you were in violation of the guidelines, you can request a review by following these instructions.
\ If you were never given the option to request a review or you’ve appealed Instagram’s decision twice and your content still hasn’t been restored, you can try escalating the issue to the Oversight Board, an organization formed to act as an independent arbiter of precedent-setting moderation decisions. The Board doesn’t take up every case that’s submitted to it, and it can move slowly, but its decisions do make a difference: In December 2023, the Board reversed two moderation decisions dealing with videos of hostages kidnapped from Israel and the aftermath of an Israeli strike on Al-Shifa Hospital.
\ If you did not get the option to request a review on deleted posts, you can submit an appeal directly on the board’s website.
\ During our investigation, The Markup found that people were not given the option to appeal the decision when their activity was categorized as “spam.” Several people who posted comments criticizing the Israel–Hamas war had their comments deleted for being spam. Meta spokesperson Dani Lever denied that Instagram purposefully categorizes some user content as spam.
\ Also published here
\ Photo by Martino Pietropoli on Unsplash
2025-12-06 03:00:00
A new report from developer analytics firm DX reveals that while AI coding tools may enhance productivity for developers, quality concerns remain.
2025-12-06 01:51:39
Dubai, United Arab Emirates, December 5th, 2025/Chainwire/--Bybit, the world’s second-largest cryptocurrency exchange by trading volume, showcases the latest monthly performance update of its Private Wealth Management (PWM) division, with the top-performing fund recording 29.72% APR in November 2025.
With wild swings across markets in the past month, Bybit PWM continued to deliver robust returns for high-net-worth clients with a disciplined, multi-strategy, and data-informed approach.
In the latest Bybit PWM newsletter for November 2025, Bybit PWM demonstrated consistent strength across its portfolio:
USDT-based strategies: Average APR of 9.8%
BTC-based strategies: Average APR of 18.09%
"Our clients depend on us to navigate volatile market conditions while maintaining focus on long-term wealth creation," said Jerry Li, Head of Financial Products & Wealth Management at Bybit.
\
"The November results demonstrate that disciplined, professional wealth management can deliver consistent returns and help our customers rise above market sentiments and distractions."
Fig. Bybit PWM Strategy Return Trend
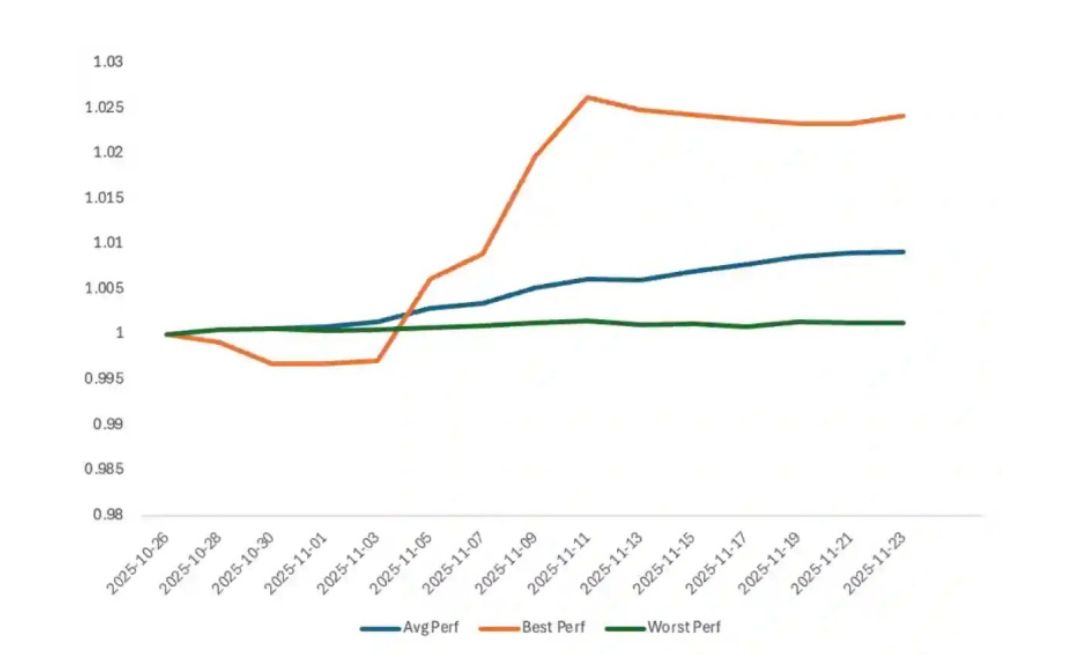
Source: Bybit Private Wealth Management November 2025 newsletter
Fund performance was calculated using Time-Weighted Return (TWR) methodology with assets aligned as of October 25, 2025, and benchmarked against funding arbitrage performance.
Bybit PWM provides high-net-worth clients with exclusive, customized wealth management services tailored to the unique demands of digital asset investors. The platform offers:
For details of Bybit PWM’s September performance, users may visit: Bybit Private Wealth Management: November 2025 Newsletter
Bybit PWM is currently offering a special year-end opportunity for our eligible VIP clients. For a limited time, the minimum subscription requirement for the PWM solution has been halved to 250,000 USDT.
Qualified investors interested in exploring Bybit Private Wealth Management services may visit: Bybit Private Wealth Management
#Bybit / #TheCryptoArk / #IMakeIt
Bybit is the world’s second-largest cryptocurrency exchange by trading volume, serving a global community of over 70 million users. Founded in 2018, Bybit is redefining openness in the decentralized world by creating a simpler, open, and equal ecosystem for everyone.
With a strong focus on Web3, Bybit partners strategically with leading blockchain protocols to provide robust infrastructure and drive on-chain innovation. Renowned for its secure custody, diverse marketplaces, intuitive user experience, and advanced blockchain tools, Bybit bridges the gap between TradFi and DeFi, empowering builders, creators, and enthusiasts to unlock the full potential of Web3. Discover the future of decentralized finance at Bybit.com.
For more details about Bybit, please visit Bybit Press
For media inquiries, please contact: [email protected]
For updates, please follow: Bybit's Communities and Social Media
Discord | Facebook | Instagram | LinkedIn | Reddit | Telegram | TikTok | X | Youtube
Head of PR
Tony Au
Bybit
:::tip This story was published as a press release by Chainwire under HackerNoon’s Business Blogging Program. Do Your Own Research before making any financial decision.
:::
\
2025-12-06 01:23:59
Meanwhile, the worldwide battle for AI productivity ecosystems has intensified at a breakneck pace.
Transcription tools whose capabilities were once limited to the simplest recording can now even reason, think, and generate content independently.
As competition grows more fierce, two questions emerge: first, which AI meeting tool will be the defining one in this next era of work?
A fresh newcomer has arrived. And it‘s not just another note-taker.
TicNote.ai is positioning itself as the world's first Agentic OS innovation that, if successful, could impact how people in various professions capture and understand what they capture.
Traditional AI tools capture what you say. TicNote helps clarify what you mean.
Instead of merely storing audio or text, TicNote introduces Agentic Intelligence, AI that thinks alongside you rather than after the fact. Every meeting, conversation, thought, or brainstorming moment becomes structured knowledge that you can search, query, and build upon.
This marks a shift from:
TicNote isn’t aiming to compete in the old category of AI note-takers. \n It’s defining a new one.
Record audio, snap images, and upload documents — TicNote’s multimodal AI instantly transforms them into:
This makes it ideal for professionals, creators, students, and researchers who need information processed, not just stored.
TicNote lets you ask questions across:
It searches across your saved recordings and documents, returning context-aware answers, a bit like revisiting your own notes with added clarity.
TicNote analyzes your collected recordings and notes, revealing patterns or relationships you might have missed. It turns scattered information into discovery — a feature especially powerful for entrepreneurs, product thinkers, and analysts.
Record a conversation and instantly convert it into a polished, podcast-style audio file. \n You can:
This is a standout feature for journalists, educators, podcasters, and creative professionals.
TicNote recognizes who is speaking and organizes notes with remarkable accuracy. \n Perfect for:
No more guessing who said what.
We live in a time of information overload, constant calls, Zoom meetings, voice messages, notes, research materials, and endless documents. The problem is no longer capturing information. It makes sense.
TicNote’s answer is Agentic Intelligence:
“The future of productivity isn’t more tools, it’s more intelligence.”
With TicNote, AI becomes more than a helper. It becomes a thinking partner.
The next productivity revolution won’t be about recording more, it will be about understanding better.
TicNote’s advantages include:
In short, TicNote isn’t competing with note-takers. \n It’s competing with the future of intelligent work.
AI meeting tools are evolving fast, but only a few are genuinely redefining how people think, work, and create. With its Agentic intelligence, multimodal capture, deep research, and insight discovery tools, TicNote AI stands out as one of the most forward-thinking devices in the space.
If the future of productivity is about turning chaos into clarity, TicNote is already ahead. Try TicNote and experience how effortless, intelligent productivity can transform the way you think, work, and create.
TicNote US store Black Friday Deal: Get TicNote at its lowest price at $99.99 from November 20 to December 1 (Amazon US store use code 0HA7G831) of the year—don’t miss it!
:::info This article is published under HackerNoon's Business Blogging program.
:::
\
2025-12-06 01:23:51
Kyrgyzstan has officially launched USDKG, a gold-backed payment access pegged 1:1 to the U.S. dollar, with an initial issue of $50 million. The access is issued on digital platform and fully audited by ConsenSys Diligence.
The issuer, OJSC Virtual Asset Issuer, is a state-owned entity under the Ministry of Finance, operating within the legal framework established by the 2022 Law on Virtual Assets of the Kyrgyz Republic. The initiative represents a first-of-its-kind model in Central Asia, merging sovereign oversight with blockchain transparency.
The launch ceremony was attended by Sadyr Japarov, President of the Kyrgyz Republic, Almaz Baketaev, Minister of Finance, and Biibolot Mamytov, CEO of Gold Dollar, the project’s operator. During the event, the dignitaries pressed a symbolic “Launch Issuance” button, officially initiating the circulation of USDKG access.
 The issuance of USDKG is carried out by a company with 100% state participation, ensuring a high level of investor trust and institutional reliability. A total of 50,000,000 USDKG have been issued, each fully backed by physical gold reserves. Operational control — including gold management — is delegated to a private company registered in the Kyrgyz Republic, under a contractual agreement with the USDKG issuer.
The issuance of USDKG is carried out by a company with 100% state participation, ensuring a high level of investor trust and institutional reliability. A total of 50,000,000 USDKG have been issued, each fully backed by physical gold reserves. Operational control — including gold management — is delegated to a private company registered in the Kyrgyz Republic, under a contractual agreement with the USDKG issuer.
The company responsible for managing USDKG’s gold reserves, has outlined plans to expand the backing to $500 million in the next phase, with a long-term target of $2 billion.
The new access is fully compliant with FATF KYC/AML standards, and redemptions require standard identity verification. It is designed to facilitate financial inclusion.
Kyrgyzstan is among the first nations in the region to establish a comprehensive digital-asset regulatory framework, setting a precedent for state-supervised virtual currencies. Government representatives emphasized that such initiatives aim to enhance economic transparency and trade efficiency, rather than serve any geopolitical agenda. Officials also noted that USDKG complements, rather than competes with, the national monetary system.
The Kyrgyz initiative underscores a broader trend toward responsible digital-asset innovation in emerging markets. The government’s focus on regulatory discipline, transparency, and tangible reserves signals a pragmatic approach to blockchain-based modernization.
With USDKG, Kyrgyzstan positions itself as a regional first-mover in regulated asset-backed digital currencies — both bridging traditional finance and blockchain infrastructure and maintaining full sovereign oversight.
Media contact
Gold Dollar — USDKG
:::info This article is published under HackerNoon's Business Blogging program.
:::
\ \ \
2025-12-06 01:23:45
Cyber intelligence rarely evolves through consensus. Real transformation begins at the margins — among analysts who quietly recognize the limitations of their tools, or within small engineering teams who see the fault lines long before the rest of the industry notices. For years, those insiders understood a truth the OSINT world seemed unwilling to confront: the individuals who pose the greatest long-term risks almost never reveal themselves through explicit signals. They don’t broadcast. They drift. Slowly. Subtly. The real “signature” of emerging risk is not a keyword or a flagged post, but the gradual erosion of coherence inside someone’s digital behavior. That long-horizon drift is the foundation of what intelligence practitioners call soft-signal intelligence, a discipline long discussed behind closed doors and now emerging as operational technology.
One of the most compelling attempts to industrialize this idea comes from a small two-year-old company operating between Tel Aviv and London: RealEye.ai. On paper, RealEye looks too early, too lean, and too underfunded to threaten legacy vendors. Yet structurally, its trajectory mirrors a pattern intelligence veterans know well. Before Palantir became a geopolitical instrument, it was a contrarian outsider — born inside the intelligence community, backed by a government-linked innovation arm, ignored by markets, embraced quietly by analysts. RealEye is not Palantir. But the rhyming architecture is unmistakable: an intelligence-native origin, early traction within agencies, support from a state-affiliated innovation program, and a willingness to challenge OSINT orthodoxy. If the next Palantir is going to ignite somewhere unexpected, Tel Aviv — with its dense national-security DNA — is one of the few plausible ignition points. And RealEye is among the rare early-stage ventures aligned with that archetype.
Where RealEye diverges sharply from legacy OSINT vendors is in its rejection of surveillance as the foundation of modern threat detection. Traditional systems still assume risk reveals itself in explicit artifacts — suspicious posts, metadata anomalies, flagged keywords. But the modern threat landscape does not behave that way. Individuals with intent adapt, sanitize, camouflage, and mimic normalcy. Their signals appear not in headlines but in micro-patterns: emotional oscillation, tightening ideological tone, narrative contradiction, shifts in worldview cadence. These soft signals rarely trigger legacy detectors, but they are the earliest indicators of escalation. RealEye’s core platform, Fortress, is engineered precisely to read these underlying evolutions.

Kevin Cohen, RealEye’s CEO and founder, expresses the paradigm shift with a clarity that functions almost as a thesis statement for the next era of intelligence:
“Surveillance shows you what a person did. Soft-signal intelligence shows you who they’re becoming. That difference is everything.”
Fortress does not care about a user’s volume of posts. It cares about the direction of their identity — how their worldview, temperament, ideology, and emotional behavior shift across months or years.
To operationalize this, RealEye built SAMS — Semi-Active Monitoring Systems. Rather than scraping everything continuously and overwhelming analysts, SAMS remains dormant unless a person begins to drift off baseline. Most digital identities remain stable; those who don’t leave faint but measurable traces. When a persona’s emotional, linguistic, or ideological patterns begin to shift, SAMS activates not to collect more, but to interpret more deeply. It approaches individuals as narratives — long arcs whose deviations matter far more than their raw content.
Cohen frames the dysfunction in the current intelligence ecosystem succinctly:
“Agencies aren’t drowning in threat; they’re drowning in noise. The real crisis isn’t data shortage — it’s meaning shortage.”
That meaning lies in the trajectory of identity — not in isolated posts. And that trajectory manifests through sentiment, language, worldview, and even the person’s relationship to geopolitical events. Soft signals surface when individuals reinterpret the world around them: shifts in tone toward political actors, conflicts, ideological movements, or polarizing events. Fortress monitors these changes with the same precision it applies to linguistic cadence or emotional volatility. The system examines how a person’s attitudes toward geopolitical tensions evolve — whether their moral framing hardens, whether sympathy toward certain factions intensifies, whether commentary on conflicts becomes more absolutist, or whether their worldview begins orbiting extreme religious interpretations or radical belief systems. These subtle, cumulative changes in worldview and attitude often precede explicit behavior by months or years. By reading the evolution of sentiment rather than the surface of statements, RealEye can surface anomalies long before legacy OSINT tools realize a shift has occurred.
Soft signals also reveal themselves through affiliations and associations — the digital company a person keeps, the ideological ecosystems they drift toward, the communities they begin orbiting. Fortress reads affiliation as a dynamic construct, mapping how individuals reposition themselves within networks, movements, or ideological groupings. The direction of association — not the mere presence of it — often exposes risk patterns invisible to traditional systems.
Hard identifiers, by contrast, are trivial to mask. Devices can be rotated. Metadata spoofed. VPNs abused. Histories disinfected. But identity drift leaks through narrative, tone, and sentiment. Fortress is designed to detect the cracks before the collapse.
RealEye’s use of large language models differs fundamentally from Silicon Valley’s chatbot paradigm. Fortress uses LLMs as analytical readers, not conversational layers. The system instructs the model to compare who a person appears to be today with who they were months or years ago — probing inconsistencies, emotional deviations, ideological shifts. It is trained not on generic internet text but on intelligence heuristics. The output resembles the beginning of an analyst brief, not a timestamped scan.
This interpretive clarity is exactly what national-security units lack today. Collection is abundant; comprehension is scarce. Intelligence units do not need more data — they need tools capable of identifying which individuals are quietly trending into high-risk trajectories.
Cohen distills the intelligence truth at the core of RealEye’s thesis:
“People can hide metadata, rotate devices, delete posts. But they can’t hide narrative drift. Identity cracks before it collapses, and that crack is what Fortress is built to detect.”
That line captures the essence of soft-signal intelligence: intent reveals itself in narrative before it reveals itself in action.
RealEye’s early adoption pattern reinforces the Palantir parallel — not in scale, but in sequence. The company emerged from within the intelligence community, not the startup world. Its first traction was with government agencies. Its early funding came from a state-affiliated innovation program focused on homeland-security capabilities. This is precisely the phase Palantir once occupied — pre-scale, pre-commercial, solving problems legacy vendors ignored.
That relevance is already appearing publicly. A recent New York Post investigation — “Robots to AI: The Technology Behind Trump’s Plan to Seal the Southern Border” — examined the new generation of homeland-security technologies and referenced RealEye’s growing role in long-horizon behavioral assessment and transnational threat detection.
Cohen is clear-eyed about RealEye’s stage:
“We’re not trying to imitate Palantir’s scale. We’re playing the stage before scale exists — the stage where clarity beats volume and precision outperforms brute force.”
Soft-signal intelligence is not a product category — it is a reorientation of the discipline. It argues that the decisive risk indicators of the next decade will come from identity evolution, ideological drift, network realignment, sentiment arcs, and worldview shifts — not from scraping deeper or surveilling more aggressively. It aligns with democratic constraints: Fortress never intrudes on private data, never hacks, never intercepts. It analyzes only what individuals willingly publish — and interprets its evolution rather than its volume.
:::info This article is published under HackerNoon's Business Blogging program.
:::
\