2026-01-20 16:30:00
If it ain't broke, don't fix it.
While I don't fully subscribe to the above quote, since I think it's important to continually improve things that aren't explicitly broken, every now and then something I use works so well that I consider it a solved problem.
In this post I'll be listing items and tools I use that work so well that I'm likely to be a customer for life, or will never have to purchase another. I've split the list into physical and digital tools and will try to keep this list as up-to-date as possible. This is both for my reference, as well as for others. If something is not listed it means I'm not 100% satisfied with what I'm currently using, even if it's decent.
I'm not a minimalist, but I do have a fairly minimalistic approach to the items I buy. I like having one thing that works well (for example, an everything pair of pants), over a selection to choose from each morning.
Some of these items are inexpensive and readily available; while some of them are pricy (but in my opinion worth it). Unfortunately sometimes it's hard to circumvent Sam Vimes boots theory of socioeconomic unfairness.

These are the products I'm using that may make the cut but I haven't used them long enough to be sure.
I like to be very intentional with my purchases. We live in an 84m^2 apartment and so everything has to have its place to avoid clutter. I understand how possessions can end up owning you, and so I try to keep them as reasonable as possible. A good general rule of thumb is that new things replace worn-out and old things, not add to them. This applies both digitally and physically, since there's only so much mental capacity for digital tools as there is for physical items.
Make things as simple as possible but no simpler.
— Albert Einstein
This list was last updated 3 weeks, 3 days ago.
2025-12-30 20:04:00
I browse the discovery feed on Bear daily, both as part of my role as a moderator, and because it's a space I love, populated by a diverse group of interesting people.
I've read the posts regarding AI-related content on the discovery feed, and I get it. It's such a prevalent topic right now that it feels inescapable, available everywhere from Christmas dinner to overheard conversation on the subway. It's also becoming quite a polarising one, since it has broad impacts on society and the natural environment.
This conversation also raises the question about popular bloggers and how pre-existing audiences should affect discoverability. As with all creative media, once you have a big-enough audience it becomes self-perpetuating that you get more visibility. Think Spotify's 1%. Conveniently, Bear is small enough that bloggers with no audience can still be discovered easily and it's something I'd like to preserve on the platform.
In this post I'll try and explain my thinking on these matters, and clear up a few misconceptions.
First off, posts that get many upvotes through a large pre-existing audience, or from doing well on Hacker News do not spend disproportionately more time on the discovery feed. Due to how the algorithm works, after a certain number of upvotes, more upvotes have little to no effect. Even a post with 10,000 upvotes won't spend more than a week on page #1. I want Trending to be equally accessible to all bloggers on Bear.
While this cap solves the problem of sticky posts, there is a second, less pressing issue: If a blogger has a pre-existing audience, say in the form of a newsletter or Twitter account, some of their existing audience will likely upvote, and that post has a good chance of feature on the Trending page.
One of the potential solutions I've considered is either making upvotes available to logged in users only, or Bear account holders receive extra weighting in their upvotes. However, due to how domains work each blog is a new website according to the browser, and so logins don't persist between blogs. This would require logging in to upvote on each site, which isn't feasible.
While I moderate Bear for spam, AI-generated content, and people breaking the Code of Conduct, I don't moderate by topic. That removes the egalitarian nature of the platform and puts up topic rails like an interest-group forum or subreddit. While I'm not particularly interested in AI as a topic, I don't feel like it's my place to remove it, in the same way that I don't feel particularly strongly about manga.
There is a hide blog feature on the discovery page. If you don't want certain blogs showing up in your feed, add them to the hidden textarea to never see them again. Similarly to how Bear gives bloggers the ability to create their own tools within the dashboard, I would like to lean into this kind of extensibility for the discovery feed, with hiding blogs being the start. Curation instead of exclusion.
This post is just a stream of consciousness of my thoughts on the matter. I have been contemplating this, and, as with most things, it's a nuanced problem to solve. If you have any thoughts or potential solutions, send me an email. I appreciate your input.
Enjoy the last 2 days of 2025!
2025-12-03 18:14:00
Quick announcement: I'll be visiting Japan in April, 2026 for about a month and will be on Honshu for most of the trip. Please email me recommendations. If you live nearby, let's have coffee?
I've always been fascinated by old, multi-generational Japanese businesses. My leisure-watching on YouTube is usually a long video of a Japanese craftsman—sometimes a 10th or 11th generation—making iron tea kettles, or soy sauce, or pottery, or furniture.
Their dedication to craft—and acknowledgment that perfection is unattainable—resonates with me deeply. Improving in their craft is an almost spiritual endeavour, and it inspires me to engage in my crafts with a similar passion and focus.
Slow, consistent investment over many years is how beautiful things are made, learnt, or grown. As a society we forget this truth—especially with the rise of social media and the proliferation of instant gratification. Good things take time.
Dedication to craft in this manner comes with incredible longevity (survivorship bias plays a role, but the density of long-lived businesses in Japan is an outlier). So many of these small businesses have been around for hundreds, and sometimes over a thousand years, passed from generation to generation. Modern companies have a hard time retaining employees for 2 years, let alone a lifetime.
This longevity stems from a counter-intuitive idea of growing slowly (or not at all) and choosing to stay small. In most modern economies if you were to start a bakery, the goal would be to set it up, hire and train a bunch of staff, and expand operations to a second location. Potentially, if you play your cards right, you could create a national (or international) chain or franchise. Corporatise the shit out of it, go public or sell, make bank.
While this is a potential path to becoming filthy rich, the odds of achieving this become vanishingly small. The organisation becomes brittle due to thinly-spread resources and care, hiring becomes risky, and leverage, whether in the form of loans or investors, imposes unwanted directionality.
There's a well known parable of the fisherman and the businessman that goes something like this:
A businessman meets a fisherman who is selling fish at his stall one morning. The businessman enquires of the fisherman what he does after he finishes selling his fish for the day. The fisherman responds that he spends time with his friends and family, cooks good food, and watches the sunset with his wife. Then in the morning he wakes up early, takes his boat out on the ocean, and catches some fish.
The businessman, shocked that the fisherman was wasting so much time encourages him fish for longer in the morning, increasing his yield and maximising the utility of his boat. Then he should sell those extra fish in the afternoon and save up until he has enough money to buy a second fishing boat and potentially employ some other fishermen. Focus on the selling side of the business, set up a permanent store, and possibly, if he does everything correctly, get a loan to expand the operation even further.
In 10 to 20 years he could own an entire fishing fleet, make a lot of money, and finally retire. The fisherman then asks the businessman what he would do with his days once retired, to which the businessman responds: "Well, you could spend more time with your friends and family, cook good food, watch the sunset with your wife, and wake up early in the morning and go fishing, if you want."
I love this parable, even if it is a bit of an oversimplification. There is something to be said about affording comforts and financial stability that a fisherman may not have access to. But I think it illustrates the point that when it comes to running a business, bigger is not always better. This is especially true for consultancies or agencies which suffer from bad horizontal scaling economics.
The trick is figuring out what is "enough". At what point are we chasing status instead of contentment?
A smaller, slower growing company is less risky, less fragile, less stressful, and still a rewarding endeavour.
This is how I run Bear. The project covers its own expenses and compensates me enough to have a decent quality of life. It grows slowly and sustainably. It isn't leveraged and I control its direction and fate. The most important factor, however, is that I don't need it to be something grander. It affords me a life that I love, and provides me with a craft to practise.
2025-11-13 16:56:00
As outlined in my previous two posts: scrapers are, inadvertently, DDoSing public websites. I've received a number of emails from people running small web services and blogs seeking advice on how to protect themselves.
This post isn't about that. This post is about fighting back.
When I published my last post, there was an interesting write-up doing the rounds about a guy who set up a Markov chain babbler to feed the scrapers endless streams of generated data. The idea here is that these crawlers are voracious, and if given a constant supply of junk data, they will continue consuming it forever, while (hopefully) not abusing your actual web server.
This is a pretty neat idea, so I dove down the rabbit hole and learnt about Markov chains, and even picked up Rust in the process. I ended up building my own babbler that could be trained on any text data, and would generate realistic looking content based on that data.
Now, the AI scrapers are actually not the worst of the bots. The real enemy, at least to me, are the bots that scrape with malicious intent. I get hundreds of thousands of requests for things like .env, .aws, and all the different .php paths that could potentially signal a misconfigured Wordpress instance.
These people are the real baddies.
Generally I just block these requests with a 403 response. But since they want .php files, why don't I give them what they want?
I trained my Markov chain on a few hundred .php files, and set it to generate. The responses certainly look like php at a glance, but on closer inspection they're obviously fake. I set it up to run on an isolated project of mine, while incrementally increasing the size of the generated php files from 2kb to 10mb just to test the waters.
Here's a sample 1kb output:
<?php wp_list_bookmarks () directly, use the Settings API. Use this method directly. Instead, use `unzip_file() {
return substr($ delete, then click “ %3 $ s object. ' ), ' $ image
*
*
*
* matches all IMG elements directly inside a settings error to the given context.
* @return array Updated sidebars widgets.
* @param string $ name = "rules" id = "wp-signup-generic-error" > ' . $errmsg_generic . ' </p> ';
}
/**
* Fires at the end of the new user account registration form.
*
* @since 3.0.0
*
* @param WP_Error $errors A WP_Error object containing ' user_name ' or ' user_email ' errors.
*/
do_action( ' signup_extra_fields ', $errors );
}
/**
* Validates user sign-up name and email.
*
* @since MU (3.0.0)
*
* @return array Contains username, email, and error messages.
* See wpmu_validate_user_signup() for details.
*/
function validate_user_form() {
return wpmu_validate_user_signup( $_POST[' user_name '], $_POST[' user_email '] );
}
/**
* Shows a form for returning users to sign up for another site.
*
* @since MU (3.0.0)
*
* @param string $blogname The new site name
* @param string $blog_title The new site title.
* @param WP_Error|string $errors A WP_Error object containing existing errors. Defaults to empty string.
*/
function signup_another_blog( $blogname = ' ', $blog_title = ' ', $errors = ' ' ) {
$current_user = wp_get_current_user();
if ( ! is_wp_error( $errors ) ) {
$errors = new WP_Error();
}
$signup_defaults = array(
' blogname ' => $blogname,
' blog_title ' => $blog_title,
' errors ' => $errors,
);
}
I had two goals here. The first was to waste as much of the bot's time and resources as possible, so the larger the file I could serve, the better. The second goal was to make it realistic enough that the actual human behind the scrape would take some time away from kicking puppies (or whatever they do for fun) to try figure out if there was an exploit to be had.
Unfortunately, an arms race of this kind is a battle of efficiency. If someone can scrape more efficiently than I can serve, then I lose. And while serving a 4kb bogus php file from the babbler was pretty efficient, as soon as I started serving 1mb files from my VPS the responses started hitting the hundreds of milliseconds and my server struggled under even moderate loads.
This led to another idea: What is the most efficient way to serve data? It's as a static site (or something similar).
So down another rabbit hole I went, writing an efficient garbage server. I started by loading the full text of the classic Frankenstein novel into an array in RAM where each paragraph is a node. Then on each request it selects a random index and the subsequent 4 paragraphs to display.
Each post would then have a link to 5 other "posts" at the bottom that all technically call the same endpoint, so I don't need an index of links. These 5 posts, when followed, quickly saturate most crawlers, since breadth-first crawling explodes quickly, in this case by a factor of 5.
You can see it in action here: https://herm.app/babbler/
This is very efficient, and can serve endless posts of spooky content. The reason for choosing this specific novel is fourfold:
I made sure to add noindex,nofollow attributes to all these pages, as well as in the links, since I only want to catch bots that break the rules. I've also added a counter at the bottom of each page that counts the number of requests served. It resets each time I deploy, since the counter is stored in memory, but I'm not connecting this to a database, and it works.
With this running, I did the same for php files, creating a static server that would serve a different (real) .php file from memory on request. You can see this running here: https://herm.app/babbler.php (or any path with .php in it).
There's a counter at the bottom of each of these pages as well.
As Maury said: "Garbage for the garbage king!"
Now with the fun out of the way, a word of caution. I don't have this running on any project I actually care about; https://herm.app is just a playground of mine where I experiment with small ideas. I originally intended to run this on a bunch of my actual projects, but while building this, reading threads, and learning about how scraper bots operate, I came to the conclusion that running this can be risky for your website. The main risk is that despite correctly using robots.txt, nofollow, and noindex rules, there's still a chance that Googlebot or other search engines scrapers will scrape the wrong endpoint and determine you're spamming.
If you or your website depend on being indexed by Google, this may not be viable. It pains me to say it, but the gatekeepers of the internet are real, and you have to stay on their good side, or else. This doesn't just affect your search ratings, but could potentially add a warning to your site in Chrome, with the only recourse being a manual appeal.
However, this applies only to the post babbler. The php babbler is still fair game since Googlebot ignores non-HTML pages, and the only bots looking for php files are malicious.
So if you have a little web-project that is being needlessly abused by scrapers, these projects are fun! For the rest of you, probably stick with 403s.
What I've done as a compromise is added the following hidden link on my blog, and another small project of mine, to tempt the bad scrapers:
<a href="https://herm.app/babbler/" rel="nofollow" style="display:none">Don't follow this link</a>
The only thing I'm worried about now is running out of Outbound Transfer budget on my VPS. If I get close I'll cache it with Cloudflare, at the expense of the counter.
This was a fun little project, even if there were a few dead ends. I know more about Markov chains and scraper bots, and had a great time learning, despite it being fuelled by righteous anger.
Not all threads need to lead somewhere pertinent. Sometimes we can just do things for fun.
2025-10-29 17:43:00
On the 25th of October Bear had its first major outage. Specifically, the reverse proxy which handles custom domains went down, causing custom domains to time out.
Unfortunately my monitoring tool failed to notify me, and it being a Saturday, I didn't notice the outage for longer than is reasonable. I apologise to everyone who was affected by it.
First, I want to dissect the root cause, exactly what went wrong, and then provide the steps I've taken to mitigate this in the future.
I wrote about The Great Scrape at the beginning of this year. The vast majority of web traffic is now bots, and it is becoming increasingly more hostile to have publicly available resources on the internet.
There are 3 major kinds of bots currently flooding the internet: AI scrapers, malicious scrapers, and unchecked automations/scrapers.
The first has been discussed at length. Data is worth something now that it is used as fodder to train LLMs, and there is a financial incentive to scrape, so scrape they will. They've depleted all human-created writing on the internet, and are becoming increasingly ravenous for new wells of content. I've seen this compared to the search for low-background-radiation steel, which is, itself, very interesting.
These scrapers, however, are the easiest to deal with since they tend to identify themselves as ChatGPT, Anthropic, XAI, et cetera. They also tend to specify whether they are from user-initiated searches (think all the sites that get scraped when you make a request with ChatGPT), or data mining (data used to train models). On Bear Blog I allow the first kinds, but block the second, since bloggers want discoverability, but usually don't want their writing used to train the next big model.
The next two kinds of scraper are more insidious. The malicious scrapers are bots that systematically scrape and re-scrape websites, sometimes every few minutes, looking for vulnerabilities such as misconfigured Wordpress instances, or .env and .aws files, among other things, accidentally left lying around.
It's more dangerous than ever to self-host, since simple mistakes in configurations will likely be found and exploited. In the last 24 hours I've blocked close to 2 million malicious requests across several hundred blogs.
What's wild is that these scrapers rotate through thousands of IP addresses during their scrapes, which leads me to suspect that the requests are being tunnelled through apps on mobile devices, since the ASNs tend to be cellular networks. I'm still speculating here, but I think app developers have found another way to monetise their apps by offering them for free, and selling tunnel access to scrapers.
Now, on to the unchecked automations. Vibe coding has made web-scraping easier than ever. Any script-kiddie can easily build a functional scraper in a single prompt and have it run all day from their home computer, and if the dramatic rise in scraping is anything to go by, many do. Tens of thousands of new scrapers have cropped up over the past few months, accidentally DDoSing website after website in their wake. The average consumer-grade computer is significantly more powerful than a VPS, so these machines can easily cause a lot of damage without noticing.
I've managed to keep all these scrapers at bay using a combination of web application firewall (WAF) rules and rate limiting provided by Cloudflare, as well as some custom code which finds and quarantines bad bots based on their activity.
I've played around with serving Zip Bombs, which was quite satisfying, but I stopped for fear of accidentally bombing a legitimate user. Another thing I've played around with is Proof of Work validation, making it expensive for bots to scrape, as well as serving endless junk data to keep the bots busy. Both of these are interesting, but ultimately are just as effective as simply blocking those requests, without the increased complexity.
With that context, here's exactly went wrong on Saturday.
Previously, the bottleneck for page requests was the web-server itself, since it does the heavy lifting. It automatically scales horizontally by up to a factor of 10, if necessary, but bot requests can scale by significantly more than that, so having strong bot detection and mitigation, as well as serving highly-requested endpoints via a CDN is necessary. This is a solved problem, as outlined in my Great Scrape post, but worth restating.
On Saturday morning a few hundred blogs were DDoSed, with tens of thousands of pages requested per minute (from the logs it's hard to say whether they were malicious, or just very aggressive scrapers). The above-mentioned mitigations worked as expected, however the reverse-proxy—which sits up-stream of most of these mitigations—became saturated with requests and decided it needed to take a little nap.
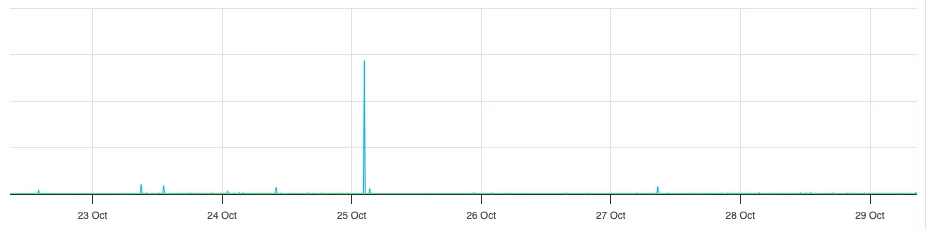
The big blue spike is what toppled the server. It's so big it makes the rest of the graph look flat.
This server had been running with zero downtime for 5 years up until this point.
Unfortunately my uptime monitor failed to alert me via the push notifications I'd set up, even though it's the only app I have that not only has notifications enabled (see my post on notifications), but even has critical alerts enabled, so it'll wake me up in the middle of the night if necessary. I still have no idea why this alert didn't come through, and I have ruled out misconfiguration through various tests.
This brings me to how I will prevent this from happening in the future.
This should be enough to keep everything healthy. If you have any suggestions, or need help with your own bot issues, send me an email.
The public internet is mostly bots, many of whom are bad netizens. It's the most hostile it's ever been, and it is because of this that I feel it's more important than ever to take good care of the spaces that make the internet worth visiting.
The arms race continues...
2025-10-22 19:23:00
Now that I've been home for about a month and have all my ducks back in a row, it's time I wrote about my trip to Istanbul for MicroConf Europe.
MicroConf is a conference for bootstrapped (non-VC-tracked) founders. And while I don't necessarily view Bear as a business, MicroConf is the closest there is to an Industry Event for someone like me.
First a note on Istanbul:
I arrived a week early to explore the city and see the sights. I'm a bit of a history nerd, so being at the crossroads of where it all happened in Europe—going back thousands of years—was quite spectacular. I get up early, and wandering the empty streets of the old city before the tour groups flooded in was quite special.
Also, the mosques dotting the skyline as viewed from the Bosporus are like nothing I've ever seen. It's amazing to see human effort geared towards creating beautiful buildings. I know it's not economically viable, but imagine if cities were built with beauty and a cohesive aesthetic in mind.
There were, however, a few negative characteristics of the city that grated at me, the main one being the hard separation of what is the tourist area and what isn't. Inside the old city all of the restaurants were clones, serving the same authentic Turkish food at 5x the reasonable price.
And scams were rife. I remember after a mediocre lunch at a mediocre restaurant, looking at the hand-written bill, the per-person cost came to about 2000TRY (roughly $50 at the time). The staff didn't speak English, and I wasn't going to throw all of my toys out of the cot via Google Translate, so I begrudgingly paid the bill and vowed never to eat there again. Similarly with taxis: it was impossible to take one as a foreigner without an attempted scam, to the extent the conference coordinator put out a PSA to use a specific transport company for rides instead of using the local taxis.
It's unfortunate when a city is unwelcoming in this manner, and it left a bad taste in my mouth.
Putting all of that aside, I still had a spectacular time. The main reason I came to this conference was to learn, get inspired, and soak up the vibes from other interesting people building interesting things. And I got exactly what I came for.
The talks and workshops were good, but what made the event shine was the in-between times spent with other attendees. The meals and walks, the hammam and sauna sessions. I found myself engaged from sunrise to sunset, notebook not far away, transcribing those notes during my downtime.
One of the attendees, Jesse Schoberg, runs a blogging platform as well, which focusses on embeddable blogs for organisations. It's called DropInBlog and is a really neat solution and platform. We chatted about what it's like running this kind of service, from bots to discoverability, and enjoyed the sunset on the terrace overlooking the Sea of Marmara. I can't think of a better place to talk shop.
I can't list all of the great conversations I had over those 3 days, but one standout to me was dinner with the ConversionFactory lads: Zach, Nick, and Corey. Not only were they one of the event sponsors, but were just great people to hang out with—and obviously incredibly proficient at their craft. After dinner on the last evening of the conference we crowded into the steam room to take advantage of the hotel's amenities that I'd paid way too much for. I got too hot, and mistaking the basin in the middle of the room for cooling off, managed to splash strong, menthol-infused water on my face. I immediately regretted it. My face, eyes, and nose started burning intensely with the icy-cold blaze of menthol and I was temporarily blinded. I had one of them hose off my face since I couldn't do anything in that state.
Product idea: Mace, but menthol.
One of my friends, Rob Hope, just arrived back from giving a talk at a conference in the US. When I met up with him for dumplings and dinner last week, it came up that, coincidentally, he had also just met the ConversionFactory lads on his most recent trip. I guess they get around.
Will I come back to MicroConf? Without a doubt. This has been inspiring, educational, and also quite validating. People were impressed with my projects, and surprised that I don't track visitors, conversions, and other important metrics. Bear is healthy, paying me a good salary while being aligned with my values, ethos, and lifestyle.
I guess I'm running on vibes, and the vibes are good.